Introduction
Nmap (network mapper) is the world's leading network security scanning tool for Linux systems. It helps identify open ports and prevents potential network security threats.
Nmap is an essential network scanning tool due to its accurate, simple-to-use, and flexible interface with many advanced features.
This guide shows how to scan for open ports on Linux systems using Nmap.
Prerequisites
- Nmap installed (see our guide for installing Nmap on Linux).
- A user with sudo privileges.
- Access to the command line/terminal.
How to Use Nmap to Check Ports
Nmap is a versatile command-line tool that performs powerful port scans. To conduct a simple scan, use the nmap command without any options:
nmap [target]The target is either a domain name or an IP address. For example, to scan the website scanme.nmap.org, use:
nmap scanme.nmap.org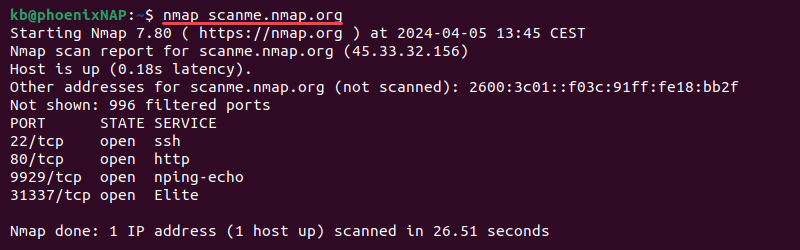
The command without any options scans the most common 1000 ports. Nmap can scan a single port, a port range, or all ports on a target. Below are step-by-step instructions on how to use Nmap to scan for open ports in various ways.
Scan a Single Port
To use Nmap to scan a single port on a target, use the following syntax:
nmap -p [port] [target]Substitute the placeholders with actual port and target values. For example, to scan port 80 on scanme.nmap.org, use:
nmap -p 80 scanme.nmap.org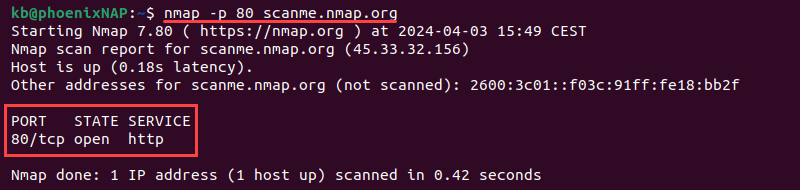
The output shows the port number and protocol (80/tcp), the port's state (open), and the service related to the port (http).
Scan All Ports
To scan all port numbers (1-65535), use the following syntax:
nmap -p- [target]For example:
nmap -p- scanme.nmap.org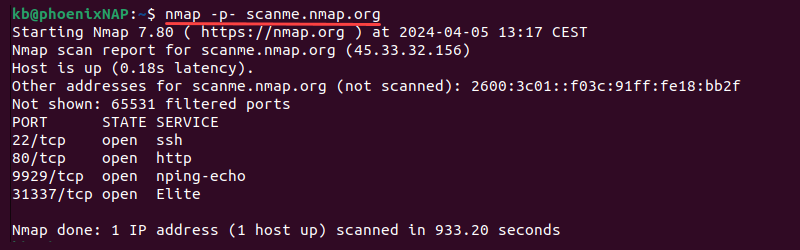
The scan takes time to complete. The command performs a comprehensive scan of all port numbers. It thoroughly assesses the target network and shows open ports for the provided location.
Alternatively, to scan all standard ports, use the fast scan with the -F tag:
nmap -F [target]For example:
nmap -F scanme.nmap.org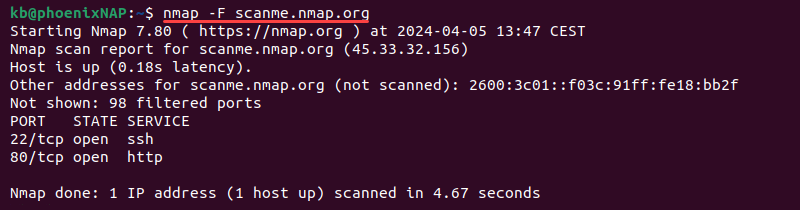
The fast scan checks the 100 most common ports. This method reduces the scan time, which is helpful with large networks.
Scan a Series of Ports
The Nmap tool offers several different ways to scan multiple ports. The examples below demonstrate how to use the tool.
To scan a port range, use the -p option, the starting and ending port numbers:
nmap -p [start]-[end] [target]For example, to scan the first 200 ports, use:
nmap -p 1-200 scanme.nmap.org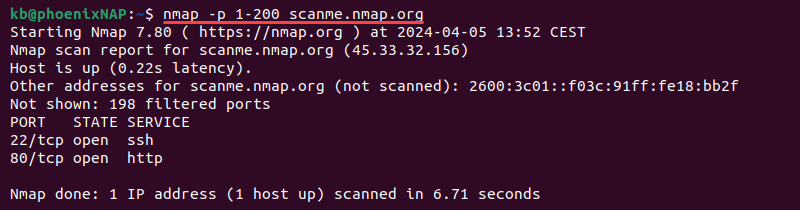
To scan multiple specific ports, use a comma-separated list:
nmap -p [port1, port2, etc] [target]For example:
nmap -p 22,53,80 scanme.nmap.org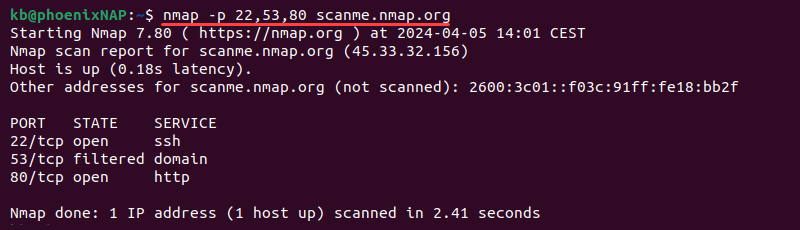
Combine the two methods to scan both specific port numbers and ranges. For example:
nmap -p 22,80,100-200 scanme.nmap.org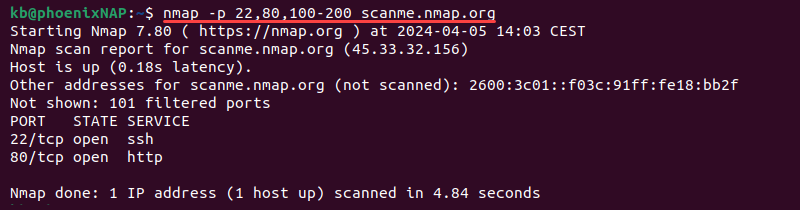
Scanning targeted ports or a port range shortens the scan time.
Common Ports
There are many standardized ports associated with specific services. Use the list below as a reference for these ports and their related service:
- 21 (FTP). File transfer protocol.
- 22 (SSH). Secure shell.
- 25 (SMTP). Simple mail transfer protocol.
- 53 (DNS). Domain name system.
- 67, 68 (DHCP). Dynamic host configuration protocol.
- 80 (HTTP). Hypertext transfer protocol.
- 110 (POP3). Post office protocol version 3.
- 123 (NTP). Network time protocol.
- 143 (IMAP). Internet access message protocol.
- 443 (HTTPS). Hypertext transfer protocol secure.
- 465 (SMTPS). SMTP secure.
- 631 (CUPS). Common Unix printing system.
- 993 (IMAPS). IMAP secure.
- 995 (POP3S). POP3 secure.
- 3306 (MySQL). MySQL database server.
- 3389 (RDP). Remote desktop protocol.
- 8080 (HTTP alternate). HTTP alternate, used for proxy servers.
Nmap helps discover port statuses and indicates how to configure a Linux firewall to block traffic on a particular port or allow some traffic.
For example, setting a firewall to block all traffic on port 80 means users won't be able to load any website. Alternatively, firewall rules can be set to allow some traffic to ports.
Use Nmap, a firewall, and other network security tools to scan traffic on a particular port and watch for suspicious activity.
Port States Recognized by Nmap
Nmap divides port status into six different states. The possible port states Nmap recognizes are:
- open. The service on the associated port is active and listens for incoming connections. The port is available for connections.
- closed. No service is listening on the port. No services are bound on the port, and the port will refuse all incoming connections.
- filtered. The port state is unknown. The port's status is concealed or restricted due to packet filtering, firewall rules, or a network security device configuration.
- unfiltered. The port state is unknown. The port is accessible and unrestricted but has no active service linked to it.
- open|filtered. The port state is open or filtered. Nmap cannot determine which due to network conditions.
- closed|filtered. The port state is closed or filtered. The exact state is indeterminate due to network conditions.
Note: Learn how to open a port in Linux.
Conclusion
After reading this guide, you have an overview of Nmap scanning and how to scan for open ports.
Next, see our server security tips that will help protect your server from various cybersecurity threats.